Understanding Homelab Network Flow: A Deep Dive into Modern Self-Hosted Architecture
An in-depth exploration of a sophisticated homelab network architecture, featuring UniFi infrastructure, Traefik, PiHole, BIND9, Authentik, and HashiCorp Vault.
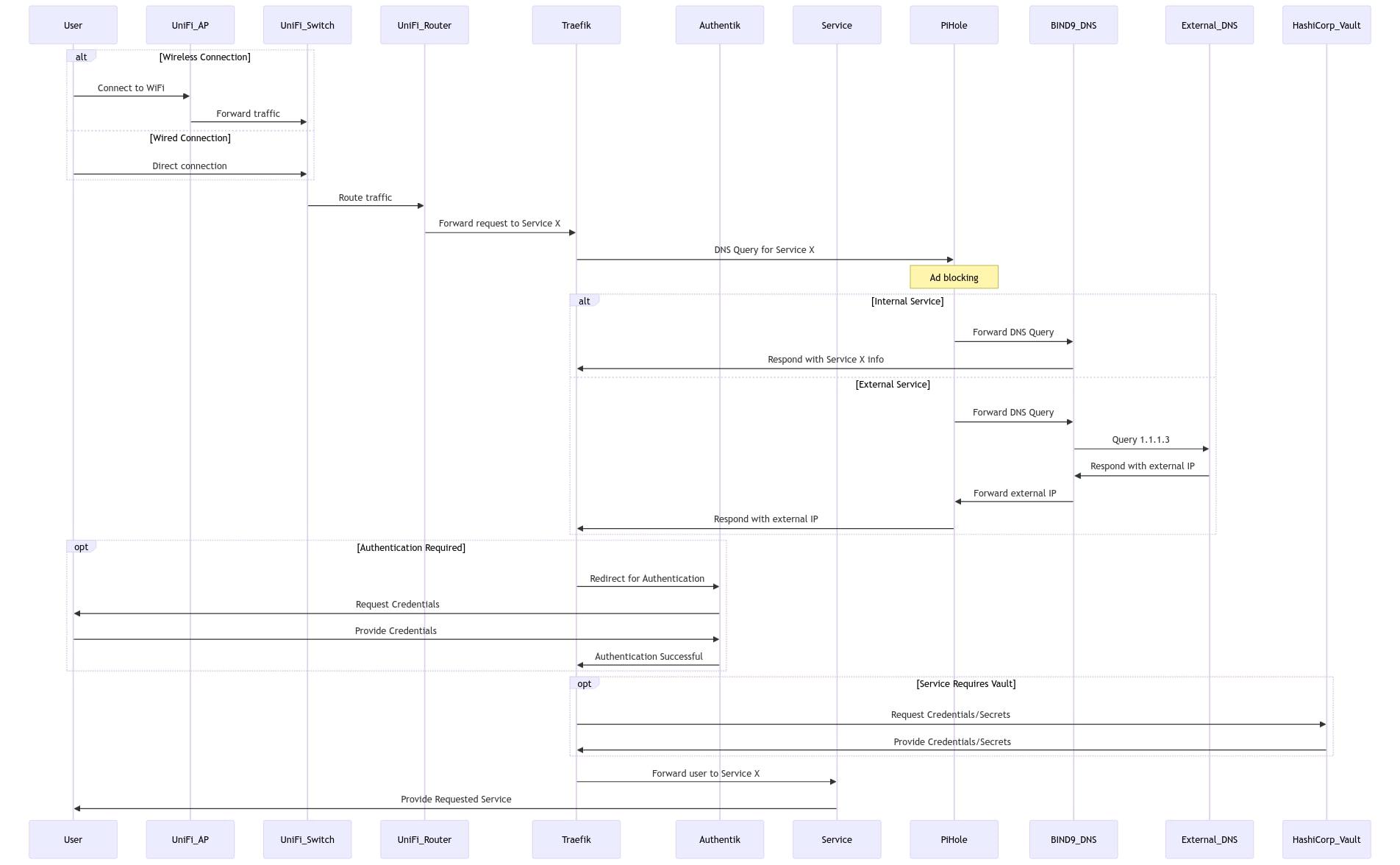
Modern homelab setups are becoming increasingly sophisticated, often rivaling enterprise-grade infrastructure. Today, I'm breaking down my homelab's network flow architecture, which demonstrates how various services interact to provide a secure, efficient, and manageable self-hosted environment.
Infrastructure Overview
My homelab architecture is built on several key components that work together to create a robust and secure network:
Network Foundation
The base infrastructure relies on UniFi components, providing enterprise-grade networking capabilities:
- UniFi Access Points for wireless connectivity
- UniFi Switch for network segmentation and management
- UniFi Router for traffic routing and network control
Service Layer
The service layer includes several critical components:
-
Traefik - Acts as the reverse proxy, handling:
- HTTPS termination
- Request routing
- Service discovery
-
PiHole - Provides network-wide ad blocking:
- DNS-level ad filtering
- Basic network analytics
-
BIND9 DNS - Manages DNS resolution:
- Internal service DNS resolution
- Forward external queries to 1.1.1.3
- Split-horizon DNS setup
-
Authentik - Handles authentication:
- Single Sign-On (SSO)
- Multi-factor authentication
- User management
-
HashiCorp Vault - Manages secrets and certificates:
- PKI management
- Secrets storage
- Credential rotation
Network Flow Analysis
The diagram illustrates several key flows:
Basic Connection Flow
- Users connect either through WiFi (UniFi AP) or direct wired connection
- Traffic is forwarded through the UniFi Switch
- The UniFi Router handles initial routing
Service Access Flow
- Requests for services are forwarded to Traefik
- DNS queries are processed through PiHole for ad blocking
- BIND9 handles DNS resolution:
- Internal services stay within the network
- External queries are forwarded to 1.1.1.3
Authentication Flow
When authentication is required:
- Traefik redirects to Authentik
- Users provide credentials
- Upon successful authentication, users are forwarded to the requested service
Secret Management
For services requiring credentials:
- Services request secrets from HashiCorp Vault
- Vault provides necessary credentials/secrets
- Services can then operate with proper authentication
Security Considerations
This architecture implements several security best practices:
- Application-level routing and load balancing with Traefik
- TLS termination and certificate management
- DNS-level ad and threat blocking
- Centralized authentication
- Secure secret management
- Network segmentation
Conclusion
This network flow architecture demonstrates how modern homelab setups can implement enterprise-grade security and management features. The combination of UniFi infrastructure, security tools, and service management creates a robust and maintainable environment for self-hosted services.
The setup is modular enough to allow for future expansion while maintaining security and manageability.